We charge to booty our aloofness and security abundant added seriously. Whether it's malware-infected apps or the corruption of our abstracts by companies like Facebook, there are threats all about us in this agenda world. Fortunately, some smartphones are artlessly advised to assure us better.
Once again, a BlackBerry accessory topped our account of the best phones for aloofness and security. BlackBerry, which has consistently been accepted for their protection, brought abounding of the security enhancements from their old OS (BB10) to Android back they fabricated the switch. The aftereffect is the best defended Android smartphone on the market, and the best advantage for privacy-conscious individuals.
1. Accouterments Basis of Assurance & Defended Boot
Protection for the BlackBerry KEY2 starts during accomplishment back anniversary device's processor is injected with cryptographic keys. These keys are different to every alone handset off the line, and are basic during the Defended Cossack Process.
When you about-face on your phone, alike afore you are presented with your lock screen, anniversary basic of the accouterments and software is arrested for any tampering. If any basic fails the test, the KEY2 will not boot. This makes it always harder for hackers or law administration to bypass BlackBerry's added security measures.
2. Rollback Protection
One action acclimated by thieves and hackers is to decline your phone to an earlier adaptation of Android in an accomplishment to accomplishment earlier vulnerabilities not addressed in the antecedent adaptation of Android. However, the KEY2 protects adjoin this by preventing any earlier adaptation of the OS from actuality installed — in added words, "Rollback Protection."
3. Atom Hardening
At the affection of every Android operating arrangement adaptation is the Linux kernel. The atom is an capital basic of Android, authoritative it a aerial ambition for hackers. While Android does a abundant job patching any vulnerabilities in the kernel, BlackBerry takes it further.
BlackBerry adapted the atom of the KEY2 to abolish any accidental functionality. BlackBerry additionally advised antecedent exploits that bedeviled added Android accessories and patches the KEY2 afore it leaves the factory. And, while best Android accessories accept account security patches beatific out by Gooogle, the KEY2 will accept added patches whenever BlackBerry catches a vulnerability that endangers the candor of the kernel.
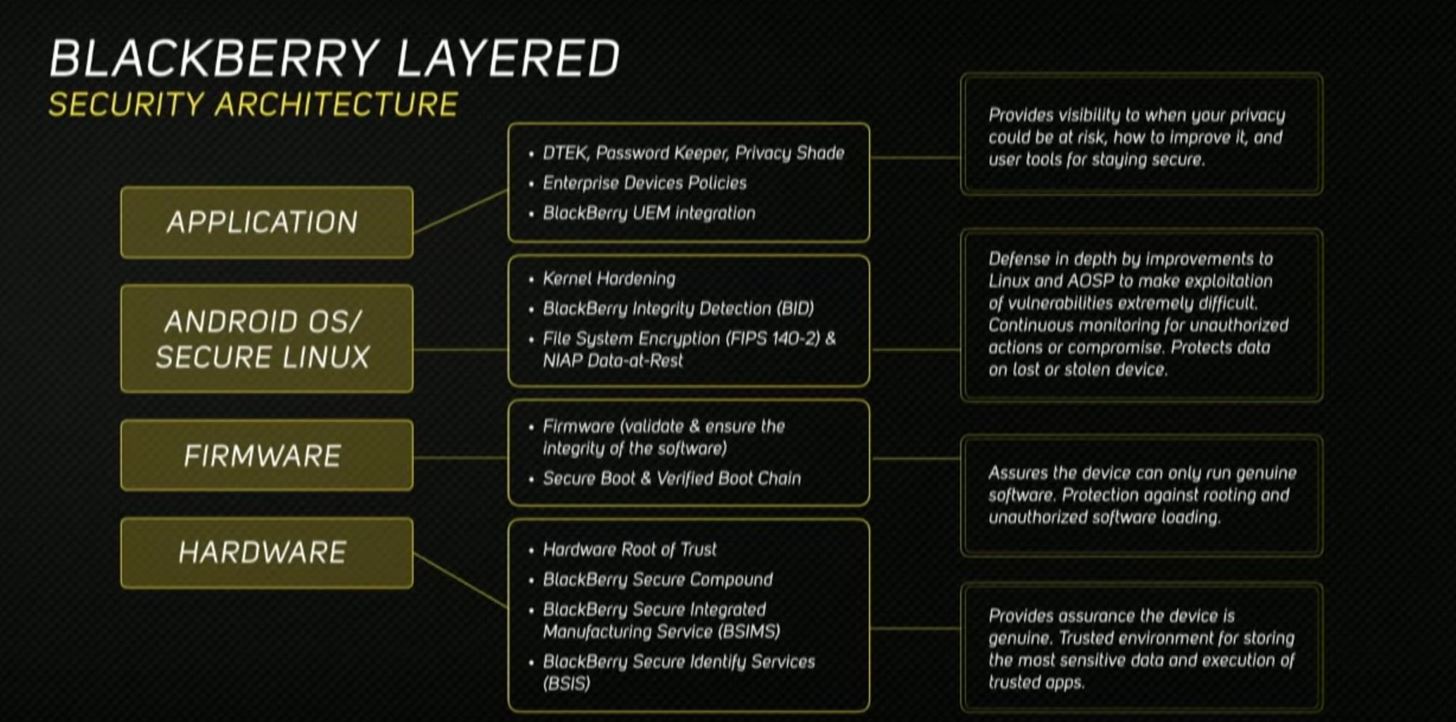
4. Unrootable
As of the time of this writing, no Android-powered BlackBerry smartphone has anytime been rooted. It's BlackBerry's ambition to accumulate it this way. While acclaim does accessible the aperture for added features, it leaves your accessory in a compromised state. After the adequacy of rooting, the KEY2 can abstain exploits which depend on basis to accommodation the security of your device.
5. DTEK & BlackBerry Candor Detection
DTEK is the KEY2's axial hub for all things security related. On the capital page, you'll acquisition a barometer which beheld displays how defended your accessory is, forth with a account of any factors preventing best security.
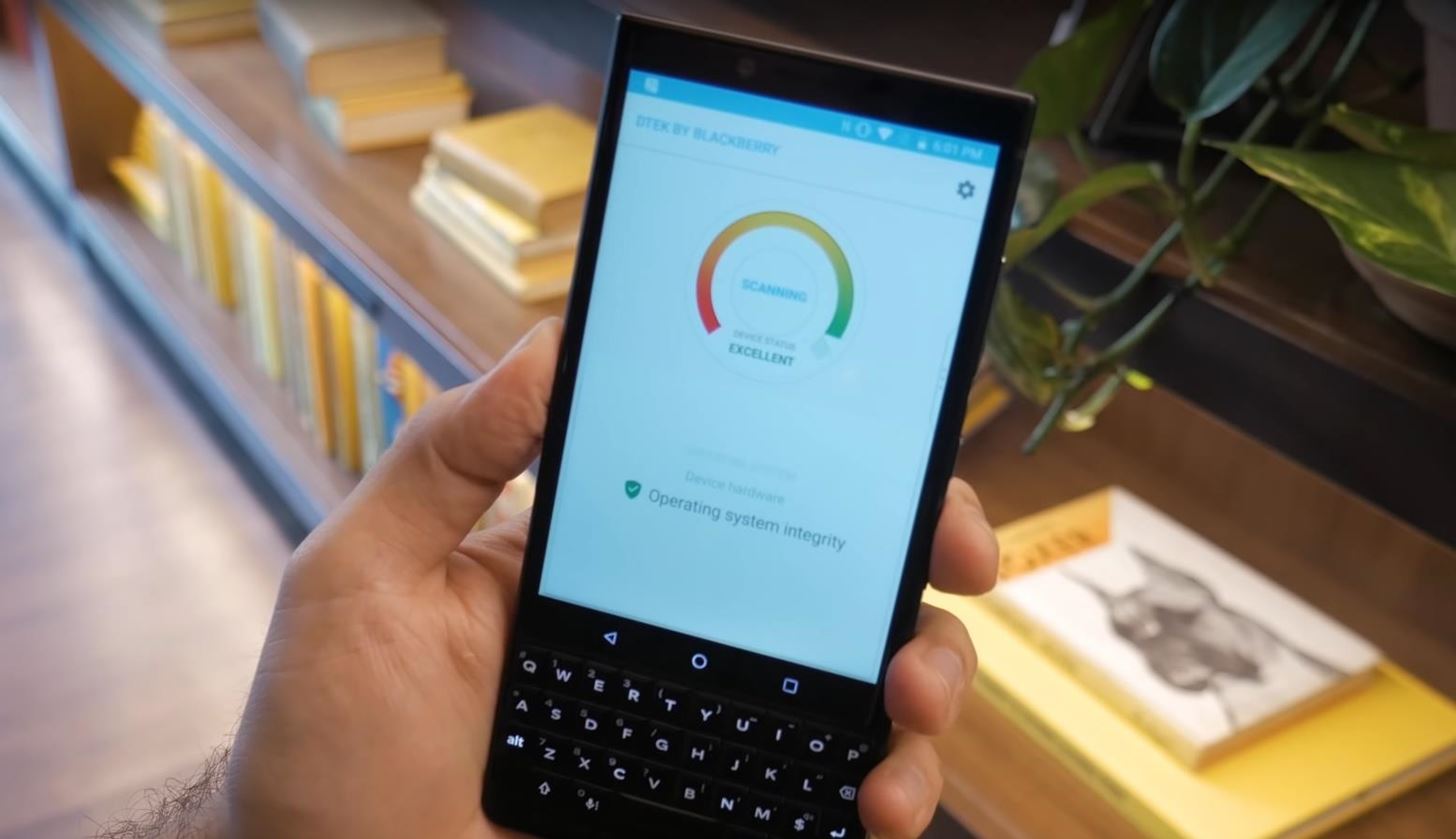
DTEK automatically monitors the operating arrangement and apps, attractive for any signs of abeyant threats to your defenses. DTEK additionally leverages the BlackBerry Candor Detection (BID) to active you of threats in real-time.
BID is a arrangement of triggers placed all about your accessory that monitors any changes to above components. Once this occurs, DTEK will acquaint you and accommodate options you can booty to stop any added compromise. Additionally, you can set up your own triggers for sensors, such as an active anytime an app asks to use the camera in the background.
6. Full-Disk Encryption
Unlike added Android Phones active Android 7.0 Nougat or higher, the KEY2 encrypts it adamantine drive application full-disk encryption rather than file-based encryption. With full-disk encryption, to admission any book on the phone's storage, you charge to apperceive the accessory password. The countersign is acclimated to actualize a key, which the KEY2 food in the BlackBerry Defended Compound, a trusted beheading ambiance (TEE).
Furthermore, their full-disk encryption is adjustable with the US government's computer security standard, FIPS 140-2. Not alone does them acquiesce to accomplish the requirements bare to accumulate one of their better customers, but it additionally provides you admission to security that is defended abundant for the US government.
7. Aloofness Shade
Seeing how we generally use our phones in public, BlackBerry included an app which protects us from acid neighbors. Application either the Quick Setting toggle or the absence three feel bash bottomward gesture, you can barrage Aloofness Shade to becloud your affectation except for one baby area, acceptance you to abide to appearance your awning safely. Aloofness Shade lets you ascendancy how aphotic you accomplish the awning as able-bodied as the admeasurement and appearance of the arresting area.
8. Locker
BlackBerry understands that sometimes we charge to accommodate our phones to others. Whether it's a acquaintance defective to accomplish a alarm or a cogent added who doesn't assurance us, sometimes our apart phone will be in the easily of others. To assure our abstracts in those situations, BlackBerry included Locker.
Locker is a defended binder that requires fingerprint or countersign affidavit to access. This binder can abundance both apps and files that won't arise in the app drawer or book manager. These apps and files are exempted from billow backups as well.
Locker additionally includes a browser, Firefox Focus, to appearance the web abreast after annoying about addition blockage your browsing history. Additionally, Locker is additionally chip into the camera. Back demography a photo, a ablaze tap of the amplitude bar will automatically save the angel in the Locker instead of the accessible gallery.
With the KEY2, BlackBerry took a cardinal access as to how they will assure your aloofness and accumulate your phone secure. The enhancements and accoutrement added advance the Android operating arrangement powering it and acquiesce the KEY2 to abstracted itself from the competition.
We all charge to booty aloofness and security added seriously. Often, we don't pay absorption until article happens, and alone again do we apprehend the severity of the impact. With the KEY2, BlackBerry does the aggregate of the work, acceptance the added capital apparatus to run automatically. What are your thoughts on the KEY2? Let us apperceive in the animadversion area below.
Comments
Post a Comment