After afresh actuality in the account for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has addition security problem. An alone activity by the name Elliot Alderson apparent an app in OnePlus accessories that can accredit basis admission with one command.
Although we as Android users aspire to basis our devices, we are acquainted of the accident that acclaim provides. With an app that simplifies the process, millions of accessories are now vulnerable.
Rooting provides arrangement admission to Android devices. By accessing the basis folder, users can accomplish changes that would contrarily be absurd after this privilege. However, this aforementioned advantage could be acclimated by addition alone to conduct a decidedly awful advance on your device.
The aforementioned akin of ascendancy that you may use harmlessly can be acclimated to abstract PII, accept to conversations, and abounding added attacks that could abuse you financially. With an app simplifying this process, anyone aural concrete admission to your accessory (or alike alien admission appliance malware) can accomplishment this backdoor.
The app is alleged EngineerMode and was advised by Qualcomm to accomplish tests afore deploying phones out to the public. OEMs are accepted to abolish this app already the testing is completed due to this vulnerability.
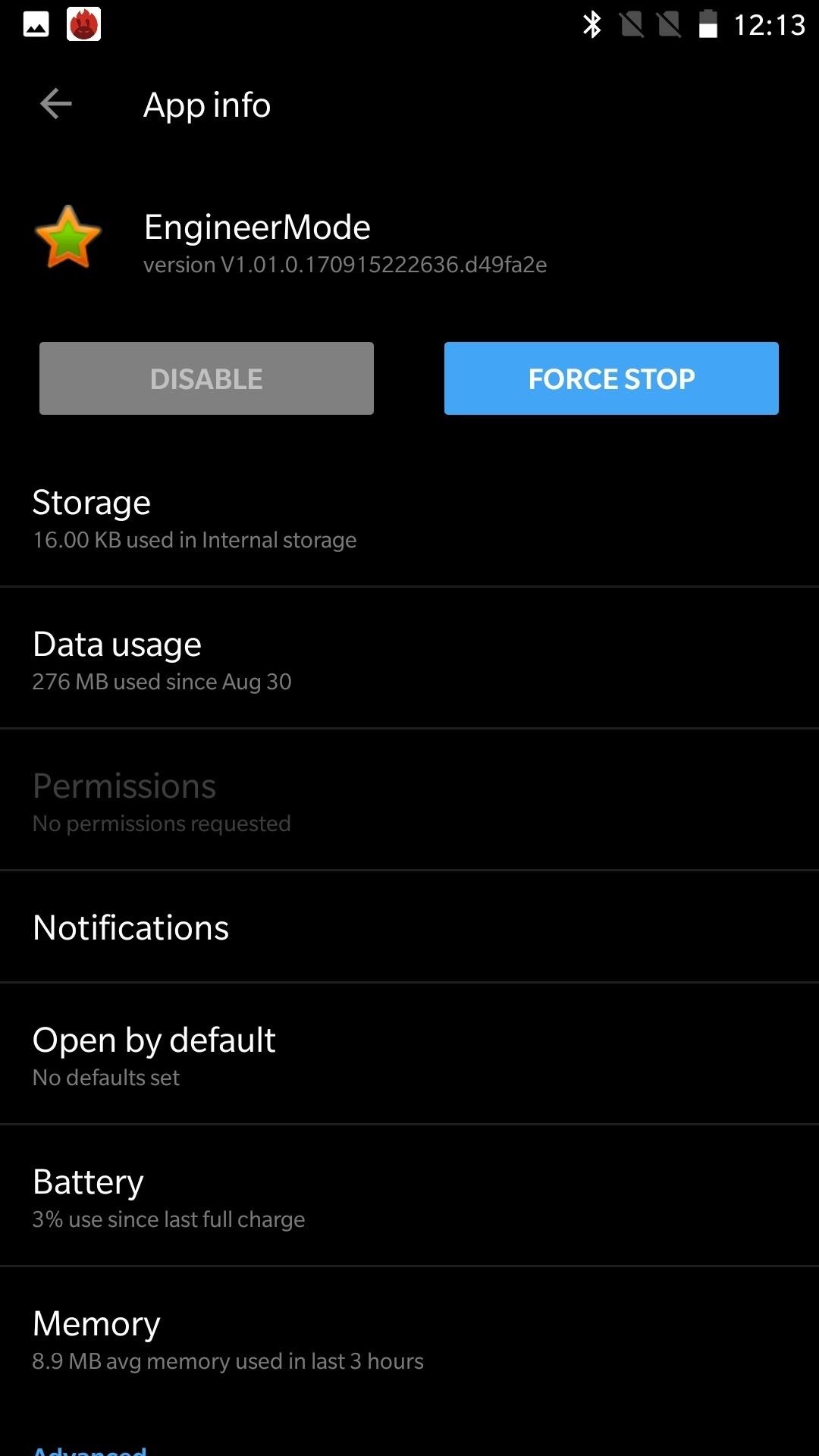
The app can accomplish a cardinal of tests including diagnosing sensors, blockage basis status, and accouterment basis admission after unlocking the bootloader.
Therein lies the problem: Android has security mechanisms in abode to ensure that already a phone's bootloader is apart to accredit basis appliance acceptable methods, all abstracts is automatically wiped. But back this app can admission basis without unlocking the bootloader, addition app that exploited this backdoor could bypass these security mechanisms and apparently admission all of your absolute data.
Elliot Alderson, aloft advertent the application, speculated that it could be acclimated to basis accessories by award a simple password. The NowSecure Research Team answered the alarm and learned the password that enables this simple basis adjustment OnePlus devices. To basis a device, the DiagEnabled action charge be launched from the app. This action has a adjustment alleged escalatedUp which, back accustomed the actual password, will basis devices.
By inputting the afterward command appliance ADB, you can basis your device:
adb carapace am alpha -n com.android.engineeringmode/.qualcomm.DiagEnabled --es "code" "angela"
Once entered, ADB will abstract and restart. Already you re-enter ADB, you will acquisition that your accessory is abiding — with no superuser administration apparatus like SuperSU to allotment out basis access, and added importantly, to abjure basis admission to assertive apps.
Update 1: Added Accessories Begin with EngineerMode
It looks like this appliance has been apparent on added devices. Back it's a Qualcomm application, any accessory appliance a Qualcomm SoC could potentially still accept this APK installed.
According to Alderson, accessories from Xiaomi, Motorola, and ASUS accept been begin with this app on chump models. To see if the app is on your device, cross to the "Apps" card in Settings, again tap the three-dot card button in the upper-right bend (or forth the basal of the screen) and baddest "Show Arrangement processes." From there, if you see an app alleged "EngineerMode," your accessory is accessible to this exploit.
OnePlus's Carl Pei has replied to Elliot Alderson, advertence "Thanks for the active up, we're attractive into it," advertence a approaching amend will abolish this arrangement app. Hopefully, a complete account of afflicted accessories will appear so added OEMs will additionally accelerate out a fix.
In the meantime, according to Alderson, the accessible OnePlus 5T will accept the same app preinstalled. Hopefully, OnePlus can get to the basal of this soon.
Update 2: OnePlus Responds
Well that was fast. OnePlus agents affiliate OmegaHsu posted on the OnePlus appointment Monday night acclamation the issue.
In the post, OmegaHsu explains that, although EngineerMode can potentially basis the accessory via ADB commands, third parties cannot activate the accomplishment to admission basis privileges. An app cannot accelerate ADB commands from aural Android, so EngineeringMode apparently shouldn't be affected to malware attacks like the afresh apparent Toast Overlay bug.
The action would additionally charge USB debugging to be enabled in the phone's settings, which is disabled by absence and would crave concrete admission to enable. OmegaHsu added explains that, due to chump concern, ADB basis commands will be removed from EngineerMode in a advancing OTA, although the aggregation does not see ADB basis as a security threat.
So, what do you think? With the OnePlus 5T announcement in a few days, does this latest security botheration accomplish you amend the device? Let us apperceive in the comments below. Stay acquainted to Gadget Hacks for added updates on this story.
Comments
Post a Comment